
Encryption
End-to-End Encryption
All communications between Devices and our Servers are End-to-End Encrypted using the latest TLS 1.3 protocol. End-to-End encryption also ensures that your data is fully encrypted when it travels between your (Client) and remote (Host) device.
Supported Encryption algorithms:
- AES-GCM 256-Bit
- ChaCha20-Poly1305 256-Bit
Comparison between two by Cloudflare.
SECURITY
Perfect Forward Secrecy
MyGreenPC uses NSA ‘Top Secret‘ grade 256-Bit AES Encryption. All communications using the CSNA compliant cipher-suite ensures Perfect Forward Secrecy (PFS) of the data.
Users can optionally switch to another modern cipher-suite: ChaCha20-Poly1305

AUTHENTICATION
Two-Factor Authentication (2FA)
Increased account protection through Two-Factor Authentication (2FA). In 2FA, users are also required to enter 6-digit code received via Email or from an Authenticator app e.g. Google Authenticator, Microsoft Authenticator etc.
Users can easily enable/disable 2FA in Account Settings. However, certain actions such as logging-in from a new device will also trigger 2FA to protect your account.
Restrict Access
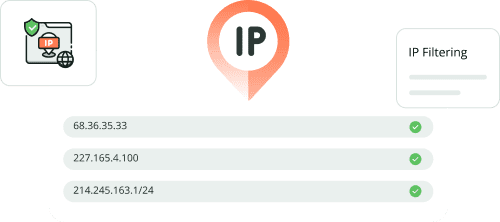
IP & Geo-Fencing
Limit account access to specific IPs and IP ranges. This ensure that people from specific IPs are allowed to access your account.
Some plans include “Geo-Fencing” feature, which allows your to restrict access based on User’s geographic location.
Registration
Account Required
MyGreenPC requires you to register & login to access a Host device and it only shows you devices that are registered in your account. This prevents your devices from mass snooping attacks that other remote access companies have experienced in the past – especially ones that allow you to connect to any device with a numeric ID.
Device Level Protection
Host Password
Host Password is an additional level of security, independent of Operating System (OS) authentication. Host Password is stored and verified at Host/Device only – even before OS credentials are verified, ensuring that no one else can even attempt to brute force OS credentials.


ROLES
Role-based Access Control
Restrict User Actions by assigning them a Role. Role-based Access Control (RBAC) ensures that each user is only able to perform allowed actions.
All Plans include two built-in Roles. Some plans allow creation of fully Custom Roles for more fine-grained access control.